
We recently had a discussion with a customer regarding the cyber security of their “fake cloud” provider for access control. They had been sold a bill of goods for an access control system that was supposed to be cloud-based. It turned out that it was not really cloud-based at all. It was simply a traditional piece of software that the company was operating on a remote server and calling it a cloud solution.
A true cloud solution is multi-tenant, scales on demand, and is pay for what you use. There is a NIST definition of true cloud computing which has been widely accepted and spells out the five essential characteristics of cloud computing. Fake clouds have none of them.
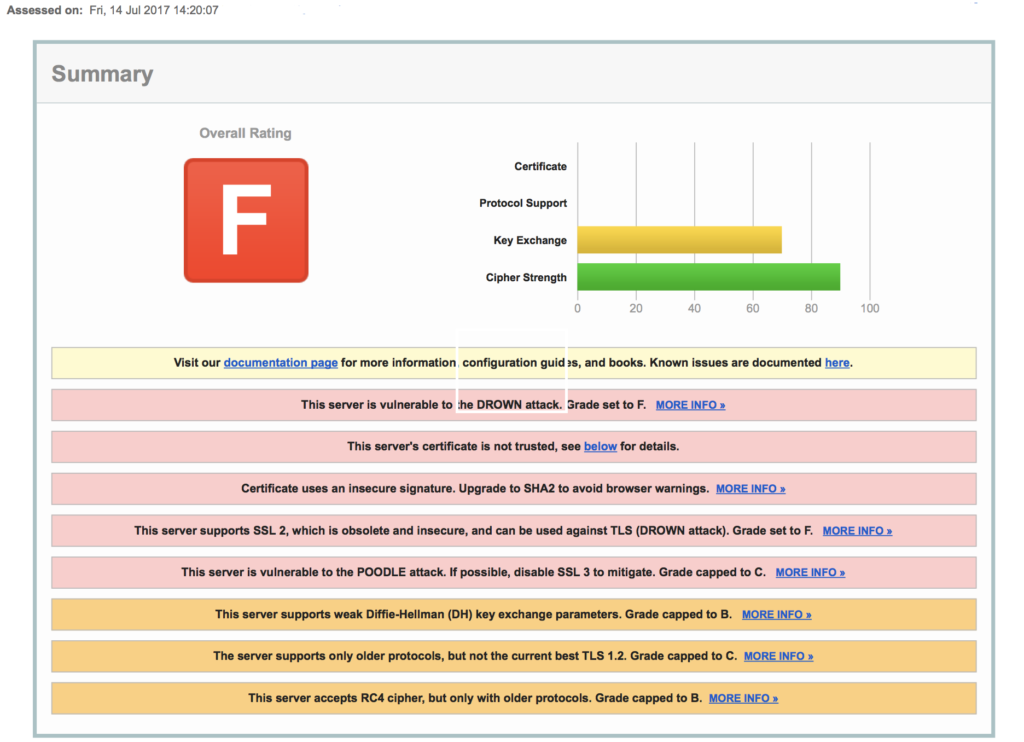
We asked our customer for the IP address of their cloud access “server” and ran a free, quick scan of its security. It was immediately categorized with an “F” for security. It’s likely any hacker could get in without trouble. That’s as unsecure as you can get. You might as well leave the front door not only unlocked but prop it open for the burglar.
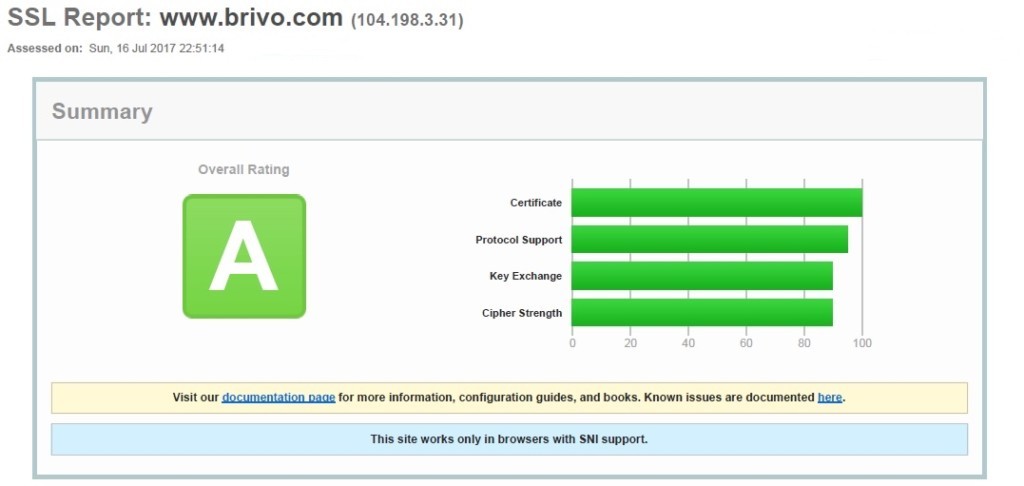
On the other hand, we ran a similar scan of the Brivo OnAir access control system. Their report is below. As you can see, it’s tight and secure. It’s managed by professionals and is a true cloud system.
Now, the problem we have in the Physical Security Industry is false claims in advertising. Here are some quotes from the fake Cloud data sheet:
- 2048 bit certificate SSL encryption
- Hardware encryption TLS 1.2 (Transport Layer Security)
- 99.999% uptime
- Distributed server architecture for security and performance
- TLS Encryption with field hardware
- Two-factor authentication
- Inherent redundancy
- Real- time Alarm Events – Zero latency
- Vulnerability Testing – Combines proven, continuous 3rd party threat monitoring and vulnerability scanning through Veracode and Amazon Web Services
That all sounds really good, but most of it’s not true and some of it is irrelevant. Here are the facts:
- They are not doing continuous 3rd party vulnerability testing. Our single amateur scan showed 10 different vulnerabilities that have not been remedied. Or perhaps they are scanning, they just are not doing anything about it!
- You can’t have ZERO LATENCY – unless you have figured out how to go faster than the speed of light.
- The report shows they are not running TLS 1.2 and instead are running older version.
- You are not going to get 99.999% uptime because they run on Amazon Web Services (AWS) and Amazon does not guarantee anything close to that – and putting multiple servers in Amazon won’t achieve it either because Amazon’s whole shebang could have trouble.
- “Inherent Redundancy?” Redundancy is never inherent – you actually have to build it.
Moral of the Story: Buyer beware. In the Physical Security world, there are charlatans selling “cloud” and “SAAS” solutions targeting the unsuspecting. You can get burned.
Words of Advice:
- Get a professional IT person to give you some advice when making your decision.
- Don’t trust everything a new vendor puts on a data sheet.
- Look at the reputation of the people running the company.
- Check references.
- Make sure it’s a TRUE CLOUD solution with real cyber security.
Other posts that might interest you

145,000 DVRs Compromised
Several articles, including one by the Wall Street Journal, have recently reported that approximately 145,000 hacked DVRs and cameras were used to create some of the largest denial of service…
September 30, 2016
Are You Afraid of Your DVR?
You should be if it's connected to the internet. It could be the doorway for hackers to access your entire network. Once a DVR is compromised, it can be used…
October 31, 2016
DDOS Cyber Attacks Update
Last week hackers forced Brian Krebs to take down his security journalism site because of a large scale Denial of Service Attack - likely one of the largest ever seen.…
September 29, 2016








